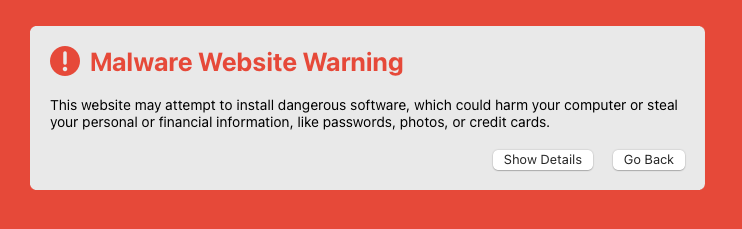
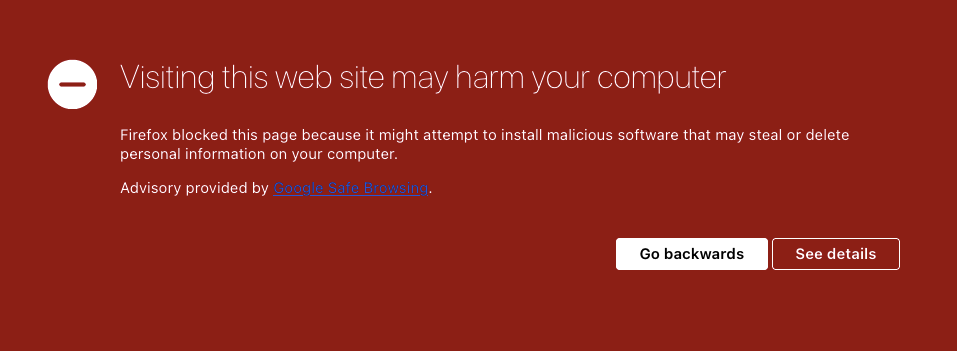
Most modern browsers (Safari, Chrome, Firefox etc.) have Google Safe Browsing built in, so that if users visit a known-harmful site, they get a prominent warning that gets their attention and tries to stop them entering their password, credit card, etc.
For example (https://testsafebrowsing.appspot.com/s/malware.html)
Safari:
Firefox:
From a privacy perspective, clearly there is a trade-off here. You can use it in a relatively private mode (https://developers.google.com/safe-browsing/v4/update-api) The terms don't (at a quick glance) seem to prohibit redistribution of this data, although you are required to use up-to-date data (i.e. no older than 30 mins) if showing warnings.
I just noticed this wasn't present, and it might be something that would keep less tech-savvy users safe. I would probably not be inclined to recommend a browser to a non-technical user that didn't have something like this built in. Although given Orion's approach to not triggering outbound connections to other services, clearly it's understandable to make a trade-off here 🙂