I've obviously never seen the source code behind Orion, but I've observed a few things about the interaction between Orion and the 1Password extensions that I'll drop here in case they're of any use.
The 1Password extensions work by inserting a chunk of javascript into every page where there is 1..n <input> elements. There may be other HTML elements or CSS selectors it looks for to know when to "hook" into a page, but I have observed it consistently with pages that contain <input> elements, if nothing else.
I'm going to preface this next section with, "As of the time of this post..."
Curiously enough, the script which 1Password injects into a page with <input> elements is called, aptly so, injected.js. As of the time of writing this, this script is ~ 360 kB in size--a mere 17,260 lines of javascript. 😏
Now, on a typical website, I rarely observe the injected.js script being loaded more than a handful of times. For example, it's only loaded once on Amazon.com, three times on Walmart.com, and twice on Reddit.com. However, the story changes dramatically on a browser benchmarking site like https://browserbench.org/Speedometer3.1. This type of site is meant to stress a browser and push it to atypical limits.
In the case of https://browserbench.org/Speedometer3.1, the script is injected/loaded 201 times in the course of one full benchmark execution (580 steps at the time of writing this). This is due to the nature of the test--the main page is loading dozens of "sub-pages" within the middle of the browser window. Each of those sub-pages may contain 1 or more <input> elements. Thus the 200+ injections of injected.js into the current tab.
But, if you're thinking to yourself, "isn't this true of all browsers? Why would this perform so poorly on Orion?" you're not alone. I don't have any complete answers, just observations. What I can see, though, is that when running the Browserbench.org test in Brave, for instance, it scores quite a bit higher than Orion. However, one difference I see is in the initiator.
In a typical browser, a javascript file load/execution will have an initiator. In the case of Brave, all 201 loads/executions of injected.js are initiated by a script called inject-content-scripts.js. I haven't dug into that script deeply at the moment, and I can't say for certainty whether that is a Brave specific script or something more generic that other browsers also use/execute. But it seems to be the same script (just incrementing VMs?) for each initiation of injected.js.
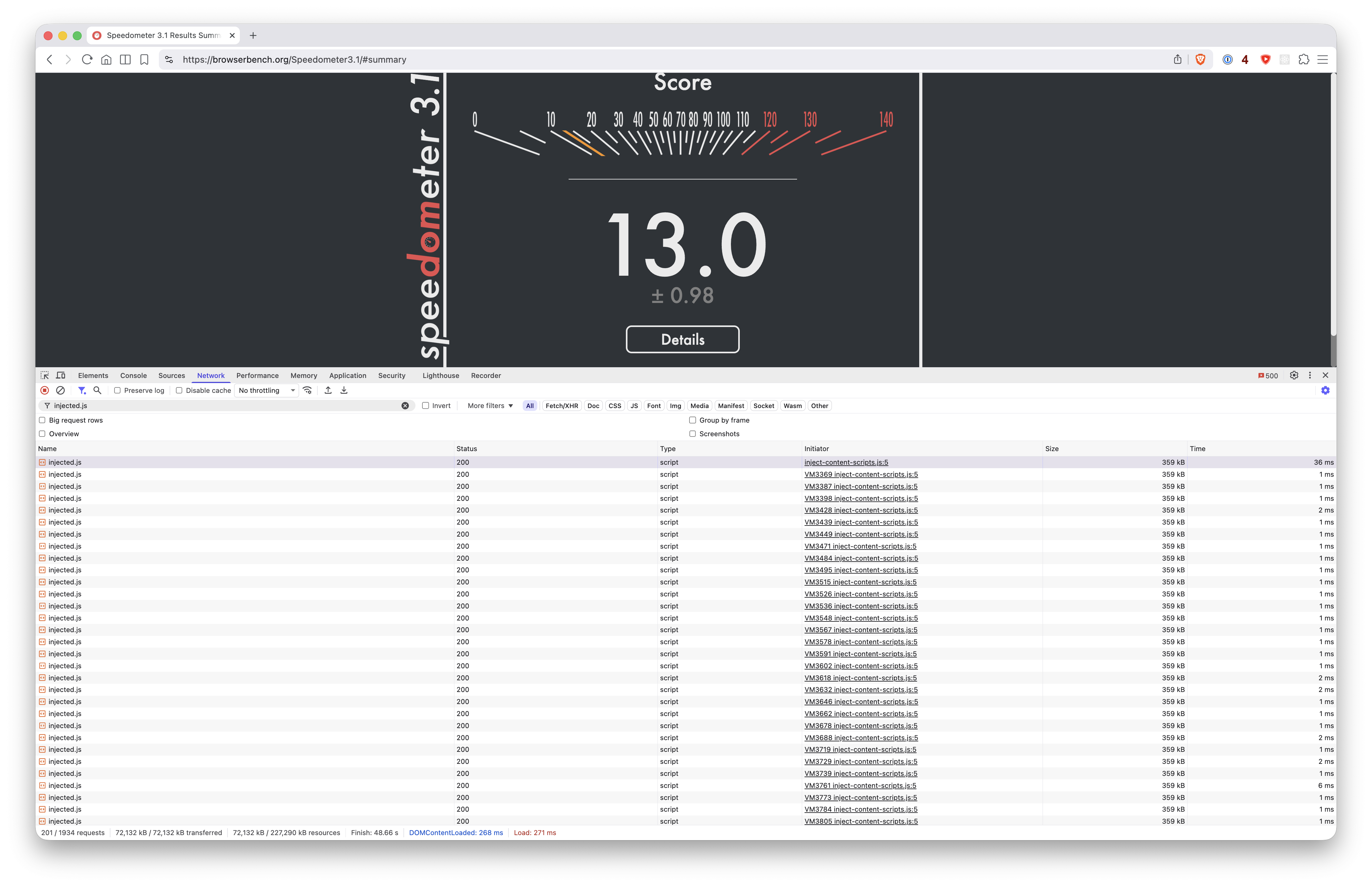
But in contrast, the 201 loads/executions of injected.js in the same Benchmark.org test in Orion are executed instead by dozens of different initiators.
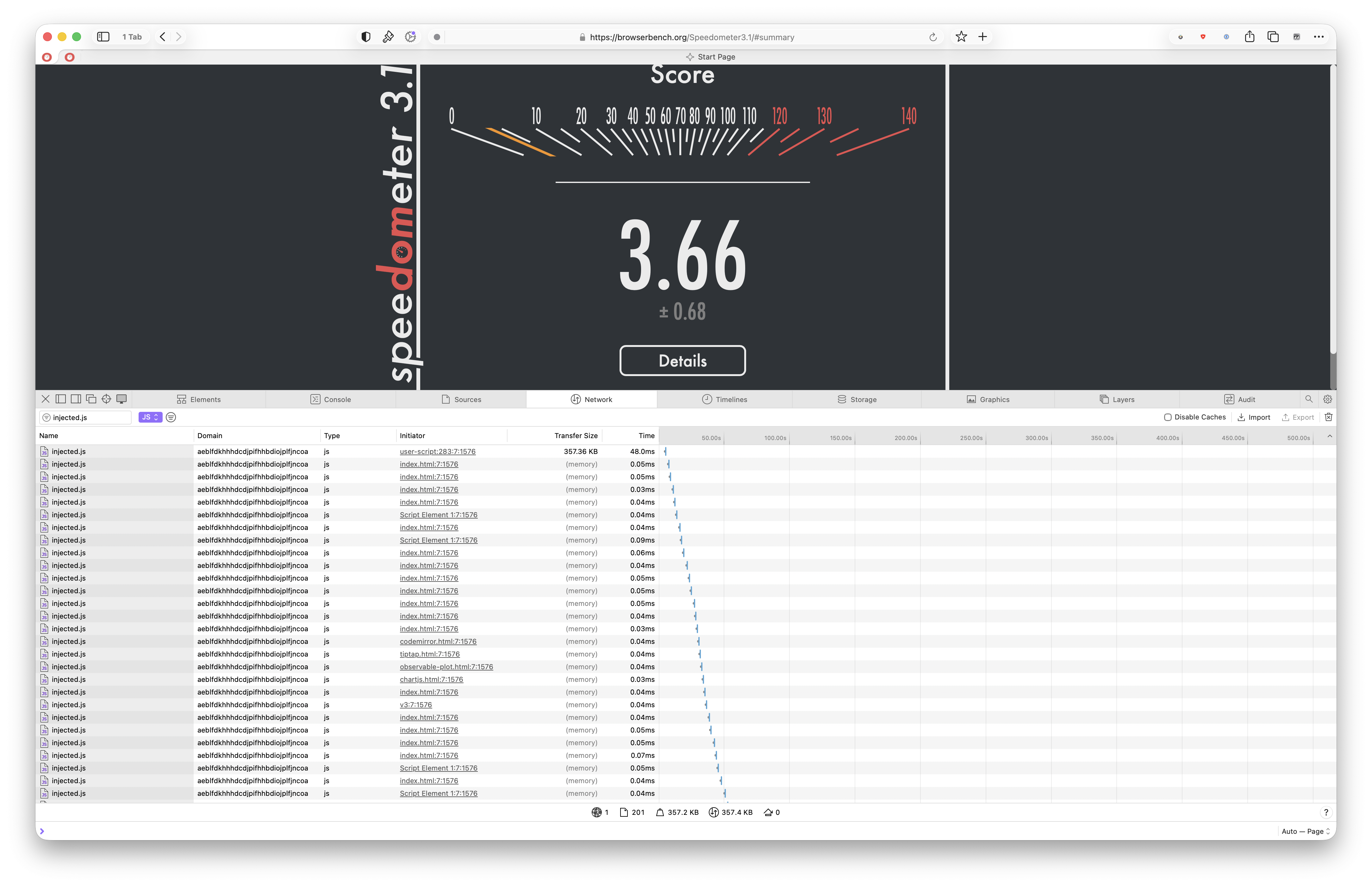
My hunch is that at the end of the day, some browsers like Brave are using some method of caching the parsed injected.js script and holding it close in memory (via VMs?) so each subsequent execution of the identical script doesn't require a re-parsing and re-interpretation of all ~ 360 kB of the same script in the same tab hundreds of times over. Perhaps this is the current difference between something like Brave and Orion? Again, those close to the Orion source code may laugh and tell me I'm off my rocker. 🙂 But from outside the black box, it's my best [somewhat educated] guesstimation at this point.
In all reality, I'm not sure the speed impact of injected.js is incredibly significant in the course of typical browsing. As I mentioned, it only seems to be loaded a small handful of times even on popular websites. The actual day-to-day impact is likely negligible--unless you're one who runs browser benchmarks on the daily. 😉
I'm not claiming that there are no interactivity issues with 1Password and Orion. Just coming to the realization that synthetic benchmark testing might not be the truest indication of a real "issue" here. Is there opportunity for Orion to optimize here--for sure! Just trying to keep this in perspective, though.
Thanks for reading!